10 Business Security Tips for Privacy Awareness Week
Updated 3 May 2022
Pronto Software is a proud supporter of Privacy Awareness Week 2022.
85% of Australians* said they have a clear understanding of why they should protect personal information – but 49% don’t know how to go about it. This is often due to the lack of time, knowledge and the perceived difficulty of “following a process”. Human error is however a significant issue for organisations – and the second largest source of notifiable data breaches. As the graph below shows, common examples range from emailing personal information to the wrong recipient to the unintended release or publication of personal information and failure to use the ‘blind carbon copy’ (BCC) function when sending group emails.
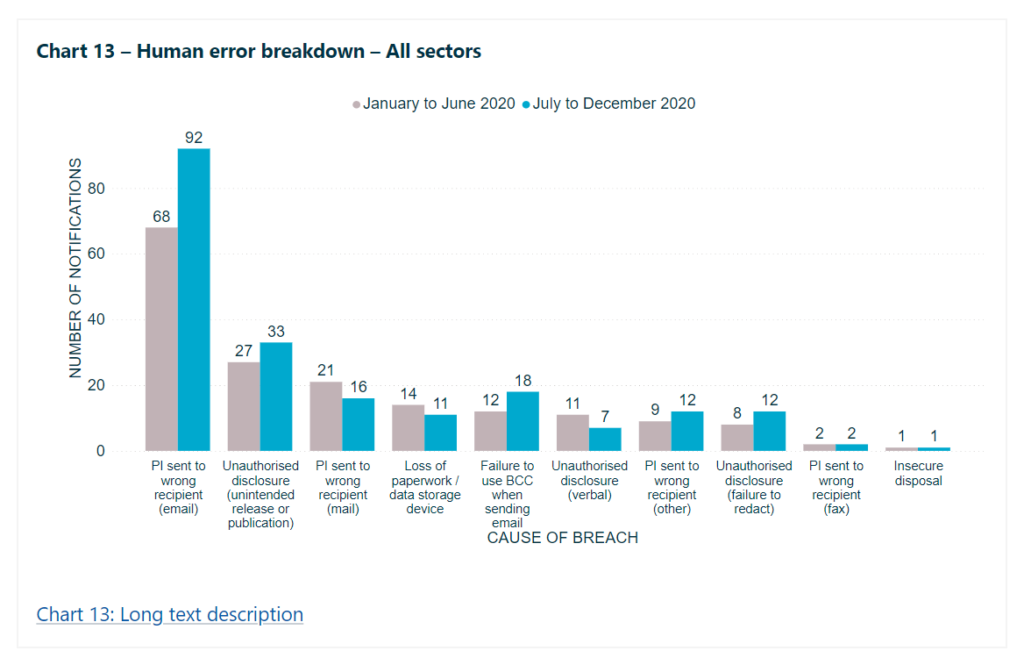
Source: ‘Notifiable data breaches report: July-December 2020‘, OAIC, 2020
The following ten tips are based on guidance from the OAIC for better security and data protection at work.
1. Prioritise staff training
Though many organisations create detailed internal policies and guidelines – time poor employees may not benefit from this knowledge. At Pronto Software, online data security awareness training uses engaging, four-minute videos to help employees understand issues – empowering them to be part of the first line of defence against sophisticated cyber criminals. There is a range of online resources available from the OAIC that help employees easily understand the risks and prevent breaches.
2. Reduce the risk of data breaches caused by human error
Many controls can be implemented such as the OAIC’s recommendation of implementing an alert that warns someone before they click ‘Send’ on an email addressed to external recipients. Some organisations have also taken steps to reduce the use of internal emails – a tool that was not designed for collaboration. Usage of workspaces such as Confluence and Jira ensure information is shared securely with the right people and reduces the email chains that clutter inboxes.
3. Physically protect personal information
Remote working can introduce new challenges for physical security. Protective measures include using authentication to ensure access is controlled, encouraging employees to lock devices before stepping away and storing/disposing of physical documents securely. Laptops or mobile phones should not be left unattended in publicly accessible shared locations. Should it be absolutely necessary to work in an open space, even for a short period, try to angle screens to minimise the opportunities for onlookers to read information.
4. Prepare a data breach response plan
The reality is that every organisation across all industries must be prepared for a data breach with a clear and practical response plan that follows four key steps: contain, assess, notify and review. Treat each data breach or suspected data breach seriously. Breaches that may initially seem minor may be more significant once full implications are assessed. Employees need to understand what actions they are expected to take to respond to a data breach so that they act in a rapid and compliant manner.
5. Put secure systems in place
ICT security measures help mitigate the risks of internal and external attackers and the damage caused by malicious software such as malware and computer viruses. These programs can be used to gain unauthorised access to business computer systems in order to disrupt or disable their operation and steal any personal information stored on those systems. The OAIC expects organisations to regularly monitor the operation and effectiveness of their ICT security measures to ensure they remain responsive to changing threats and vulnerabilities that may impact the security of personal information. This includes:
- being aware of the personal information held in the ICT system and where it is located
- providing a safe environment for staff to work and customers to interact with the business, for example when they make payments or provide their banking details and/or other personal information
- considering the security of all systems that use or interact with ICT systems – such as securing websites, social media platforms, mobile device applications (apps) along with Internet connected end-user mobile devices, portable storage devices, desktop terminals, kiosks, as well as Wi-Fi networks and remote access
6. Build in privacy by design
‘Privacy by design’ is a process for embedding good privacy practices into the design specifications and architecture of new technologies, business processes and physical infrastructures. It’s more effective and efficient to manage privacy risks proactively, rather than to retrospectively alter a product or service to address privacy issues that come to light. At Pronto Software this ethos extends to the way Pronto Xi ERP and analytics software is designed.
7. Review privacy policy
While privacy policies help Australians trust a website or service, less than a third of us read this long and complex information. Organisations who care about their customers create a privacy policy in standard, simple language – to ensure people can understand the material. It is also important to review the policy regularly and update it when privacy practices change – and the OAIC offers guidance.
8. Undertake a Privacy Impact Assessment
For projects that can put individual or customer privacy at risk, the OAIC recommends a privacy impact assessment (PIA) to explore how to manage, mitigate or eliminate privacy risk.
9. Only collect the required personal information
Ensure that the personal information (PI) collected is only used and disclosed for the intended purpose and that reasonable steps are taken to protect this information. For example, due to COVID-19, Australian states and territories are introducing legislation that requires businesses to collect personal information about visitors to business premises. Each state and territory has its own legislation in regards to what information businesses must collect. When collecting information from customers, ensure the requirements of the Australian Privacy Act are fully considered.
10. Making privacy a priority comes from the top
Embed a privacy champion at a senior level. In any organisation, a strong leadership commitment builds a culture of privacy governance. Pronto Software’s approach to privacy stems from the values of this business – it’s not a reaction to regulation. Today consumers demand full accountability and reward companies that make data privacy a central tenet of their strategy. This can even improve business productivity by driving more efficient business processes. OAIC resources can help assess practices and set realistic goals.
Sources
*’Australian Community Attitudes to Privacy Survey 2020‘, OAIC, 2020




Let's stay connected
Be the first to receive our resources, including news about your industry.


